In previous publications, we have established the benefits in maintaining a compliance dashboard for performance management, but we have not discussed how to go about building one. Building a compliance dashboard is no easy task since it requires a great deal of effort to design, create, maintain, and utilize effectively, but with modern tools it is significantly easier than in the past. The actual implementation may be discussed in a future article, but today we are focusing on the fundamental scoping priorities of building a compliance dashboard since in many ways it is the most difficult step. Much like traditional software development, the most critical stage to get right in building a compliance dashboard is requirements analysis since it’s critical to thoroughly understand the purpose, requirements, and goals of the dashboard prior to implementation. Designing a compliance dashboard without a proper understanding of what to measure is a recipe for disaster, which means that knowing the difference between measuring performance versus measuring activity is crucial.
Understanding Cybersecurity Performance Indicators
Distinguishing whether a tracked metric measures performance or activity is more than just a matter of semantics. By definition, a cybersecurity performance indicator (CPI) that tracks activity rather than performance may tell you what your team is doing, but it does not describe how well your team is doing it. As a simplistic example, let’s take a CPI that tracks the number of corporate devices that have received a vulnerability scan in the last 14 days. This number might tell you that 98% of end user devices have been scanned in the last 14 days, but it says nothing about the results of those scans or how many of those devices have a high risk or critical vulnerability. This metric may be useful for understanding how often you’re scanning known devices, but it doesn’t give you any insight into how secure those devices actually are. A compliance dashboard that is filled with surface-level CPIs that don’t elucidate much on the actual substance of cybersecurity performance is bound to look encouraging since it’s easy to tell yourself, “look at all of these metrics we’re tracking and how well we’re performing on them!” Those metrics can become misleading if they are thought to be the whole story, lulling management teams into a false sense of security. So, we know that we need to avoid relying solely on metrics that show activity rather than performance; but how do we determine what CPIs measure the latter rather than the former? Generally, these CPIs should focus on tracking things that require proactive intervention in order to remediate an identified flaw. To follow with the earlier example, a CPI that shows performance rather than activity might be one that tracks the percentage of identified “high” or “critical” vulnerabilities that have been patched on web facing devices, or key assets deemed as the “crown jewels” in the last 14 days. This is a much more valuable CPI than the example earlier because it tells a lot more about how your team is performing in their mitigation of security threats, in the case by patching x percent of high severity vulnerabilities.
What Are the Key Metrics to Track
As far as what kinds of metrics to track, the biggest must-haves for most organizations are typically vulnerability management, asset management, endpoint encryption status, patching regularity, and user access control metrics. These metrics are some of the most fundamental aspects to track when looking to improve cybersecurity performance because of the high risk associated with a failing in any one of these key areas. We’ve talked previously about how critical continuous visibility is when evaluating cybersecurity performance, and this applies here as well. Endpoint security management and vulnerability management are two of the most important CPI categories to track because of the persistent threat presented by cybercriminals targeting vulnerable end users. According to Morphisec’s 2020 Work from Home Cybersecurity Threat Index—a survey of almost a thousand office workers—49% had never worked from home before the pandemic. With 56% of remote employees also using personal devices for work purposes, it’s no surprise that a Malwarebytes publication in August reported that 20% of respondents had faced a security breach because of risky behavior from a remote worker. Scanning organizational devices for vulnerabilities, remediating identified vulnerabilities in a timely manner, and keeping track of end user device activity is crucial in maintaining a strong foundational cybersecurity performance baseline.
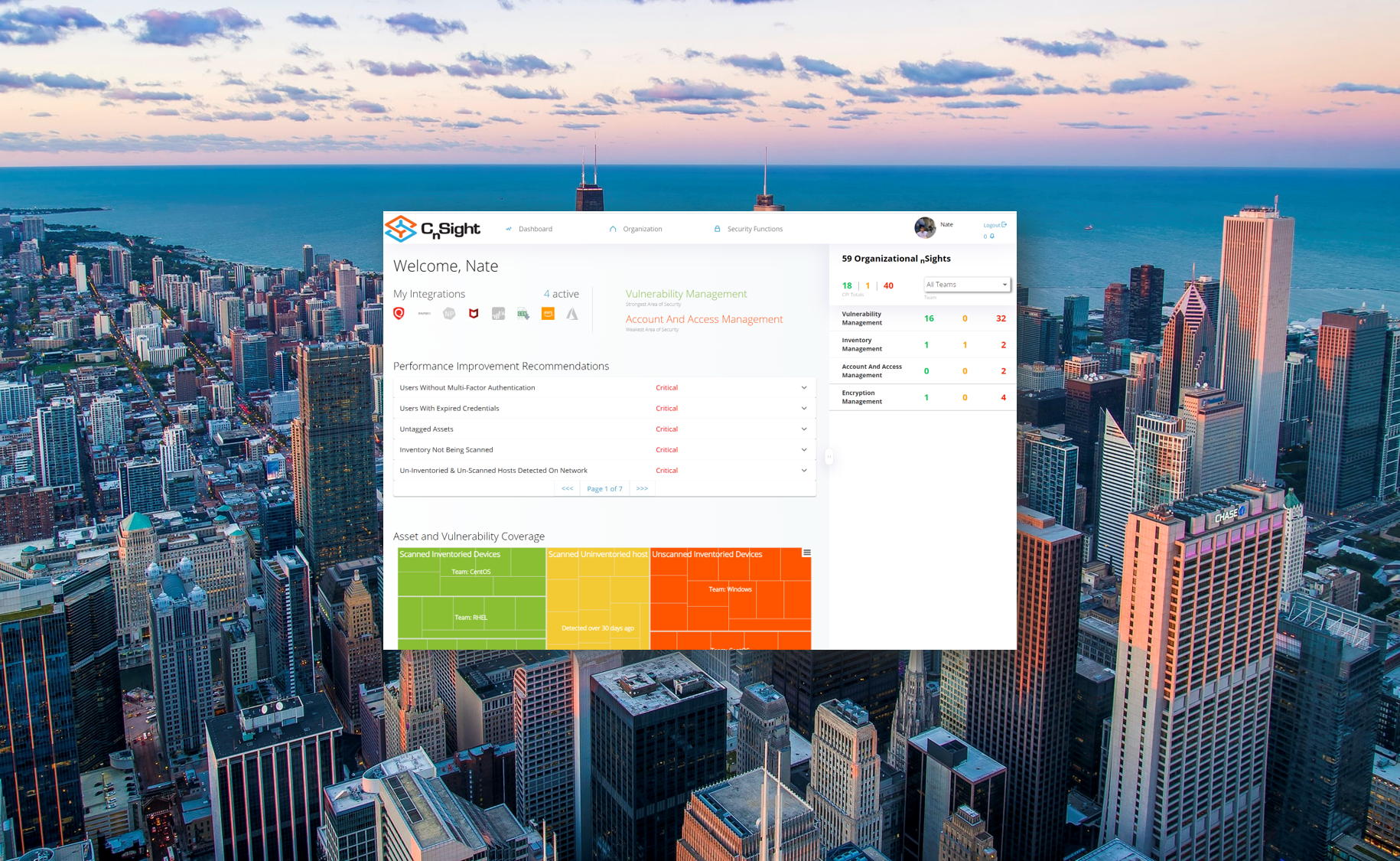
CnSight: A Compliance Dashboard with Continuous Visibility
It’s easy to talk about what you should be tracking, but it’s a lot harder to take that first step toward implementing a compliance dashboard. Thankfully, there are products like CnSight which eliminate the need to create your own dashboard from the ground up. Building a compliance dashboard without a platform like CnSight is a significant endeavor even if the project is provided generous funding, given the difficult tasks of automating data collection, building product integrations, and compiling collected data into a meaningful format. However, with compelling tools on the market that significantly lower the barrier for entry, it has become easy to significantly reduce the deployment time and the level of effort needed for an organization to incorporate a compliance dashboard into their cybersecurity performance improvement workflow.