Due to the COVID-19 pandemic many businesses have become yet more vulnerable than before to cyberattacks. Boards, CISOs, and other business executives are aware it’s not a matter of “if” but “when.” Continuous monitoring is a major trend that is part of a desire to control risk in real time. It is based in part, on SIEM (Security Information and Event Management) tooling, log management for data collection and analysis, and security dashboards for visualization.
This market known as Information Security Continuous Monitoring (ISCM) is defined as maintaining ongoing awareness of information security, vulnerabilities, and threats to support organizational risk management decisions.
There are many ways to build a continuous monitoring program (CMP), but here are a few tips and requirements on how to build a successful one.
Risk analysis
In order to build an operational CMP, the needs and risks a business faces must be evaluated and understood. If the objective is to assess in real time the company’s security posture and the evolution of its risk exposure, this requires having first carried out the necessary risk analyses and having determined the relevant control points. Each company has different needs and will need a different approach, which it why a detailed risk analysis and assessment should always be the first step.
Integration Process
One of the main challenges in building a successful CMP is to not neglect the integration process. The difficulty inherent to an ISCM project is its integration with existing systems. It will therefore often be first and foremost an integration project. In fact, no matter how great the CMP, if it can’t be correctly integrated with existing systems then it will most likely be completely useless.
Proactive
A successful CMP should not only detect breaches and incidents, it must anticipate recovery. In other words, a good CMP should not only detect incoming threats, it also has to be capable of enabling an efficient recovery process. In the event of an attack, it should ensure that the loss of information or data remains minimal.
Efficient tools
Many tools can be used in a CMP, but finding the most efficient ones is where the difficulty resides. These tools can help with dashboard management, risk reporting, real-time system-state analysis, GRC (Governance, risk and compliance refers to a strategy for managing an organization’s overall governance, enterprise risk management and compliance with regulations), and Networking Configuration Management Tools for Continuous Monitoring.
Continuous Visibility
Staying informed of the most important cybersecurity metrics and knowing how you are performing should be at the top of CISOs list. Maintaining compliance dashboard is one of the best ways to do that and can help keep track of performance and compliance data in an easily- digestible and user-friendly format.
Personalized Approach
Choosing the right tools and coming up with the right strategy when building a CMP is one of the top concerns since each business or entity has specific needs. These needs may differ greatly depending on the nature of the organization. For example, for government organizations, risk management is very different from that of a private business. In order to build a successful CMP, a range of questions such as these below should be answered beforehand.
- How much risk can this business tolerate?
- How confidential is the information that the business handles?
- What could the consequences be if this confidential information is compromised?
An ISCM project will therefore be a subtle balance between consulting and integration and between risk management (organizational) and operational (technical). If successful, a good CMP could make all the difference in the world.
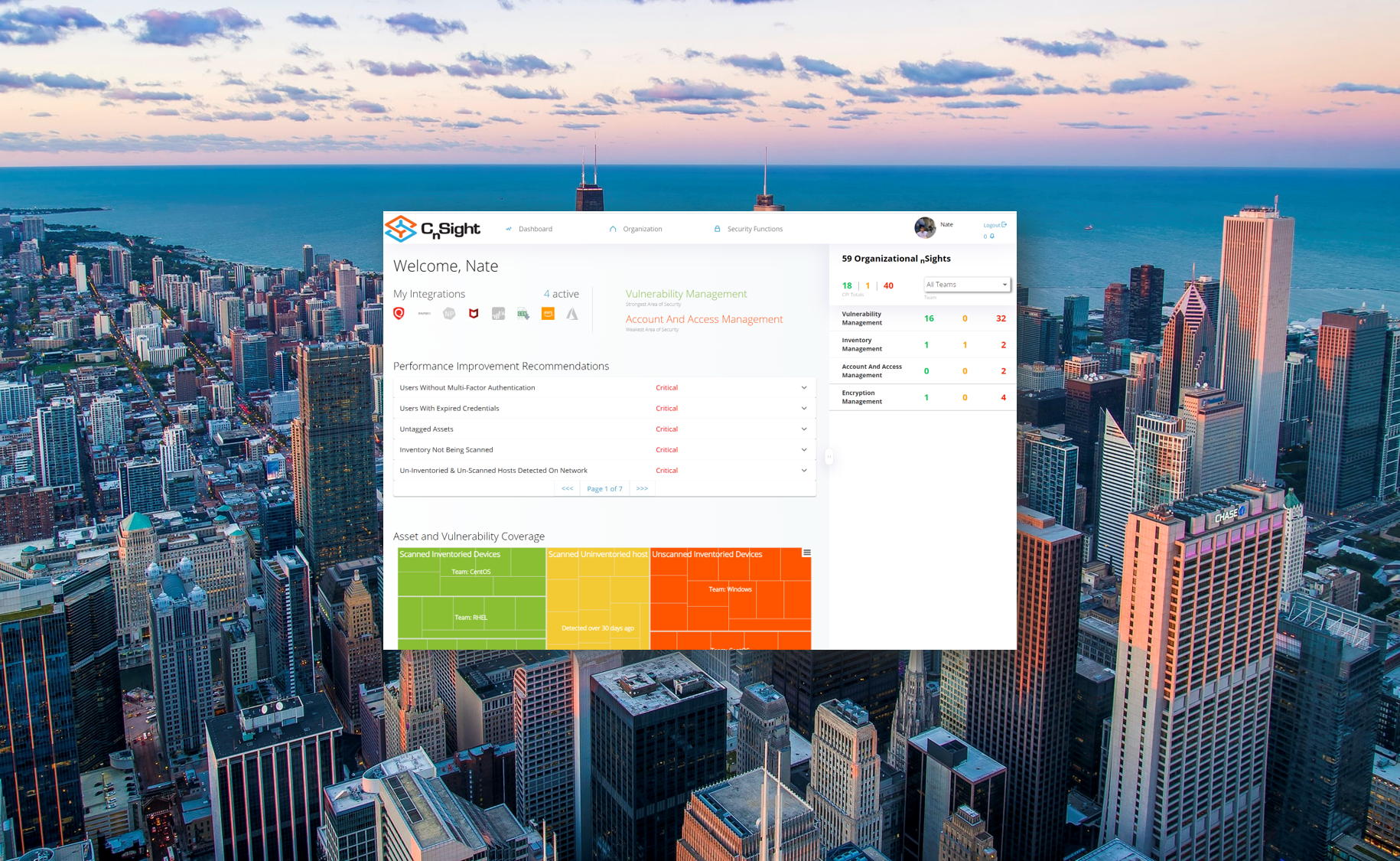
Continuous Monitoring with CnSight
At TDI we understand how important cybersecurity is to your business. Find out more about our one-of-a-kind product, CnSight, which is an executive level dashboard that provides the continuous visibility needed to understand exactly where you stand in terms of the consistency and effectiveness of your security program.