In the last few days, Microsoft disclosed a data leak that exposed 38 terabytes of company data, including passwords, Teams messages, and the backups of two Microsoft AI research employees’ workstations. Thankfully, Microsoft has confirmed that no customer data was exposed. The leak was caused by an overly permissive Shared Access Signature (SAS) token that was accidentally exposed in a public GitHub repository, giving anyone with the link the keys to the kingdom.
SAS tokens are a powerful tool for sharing data in Azure Storage, but they can also be dangerous if they are not properly configured. In this case, the SAS token gave anyone with the link access to the entire storage account, even though the researcher only intended to share a specific dataset.
The Wiz.io research team that discovered the leak was able to access the data for several days before Microsoft became aware of the issue and revoked the SAS token. Microsoft has stated that no customer data was exposed in the leak, and that the company has taken steps to prevent similar incidents from happening in the future.
This data leak is a reminder of the importance of cybersecurity best practices when using cloud computing platforms. We’ve long been advocates for the idea that you are only as good as your worst performance when it comes to cybersecurity, whether you’re a small business or an S&P Top 50 goliath. It doesn’t matter how many next-gen cybersecurity tools you have in your toolbox if you aren’t doing the basics correctly. Further, if you don’t have visibility into the day-to-day performance of your team, you can’t even tell if you’re on the right track!
Even the biggest tech giants can leave themselves vulnerable to misconfiguration and human error, but there are things you can do to minimize that risk and increase baseline cybersecurity performance. Cybersecurity Performance Management (CPM), as championed by TDI, is a transformative evolution in cybersecurity teams that allows organizations to track, measure, and optimize their cybersecurity performance. Here are a few things that organizations can do to implement CPM and reduce the risk of data leaks:
- Establish meaningful KPIs that are important to your organization. Every organization will have different cyber priorities, so what metrics are worth tracking will always vary. Identify your top priorities and figure out how you can measure them.
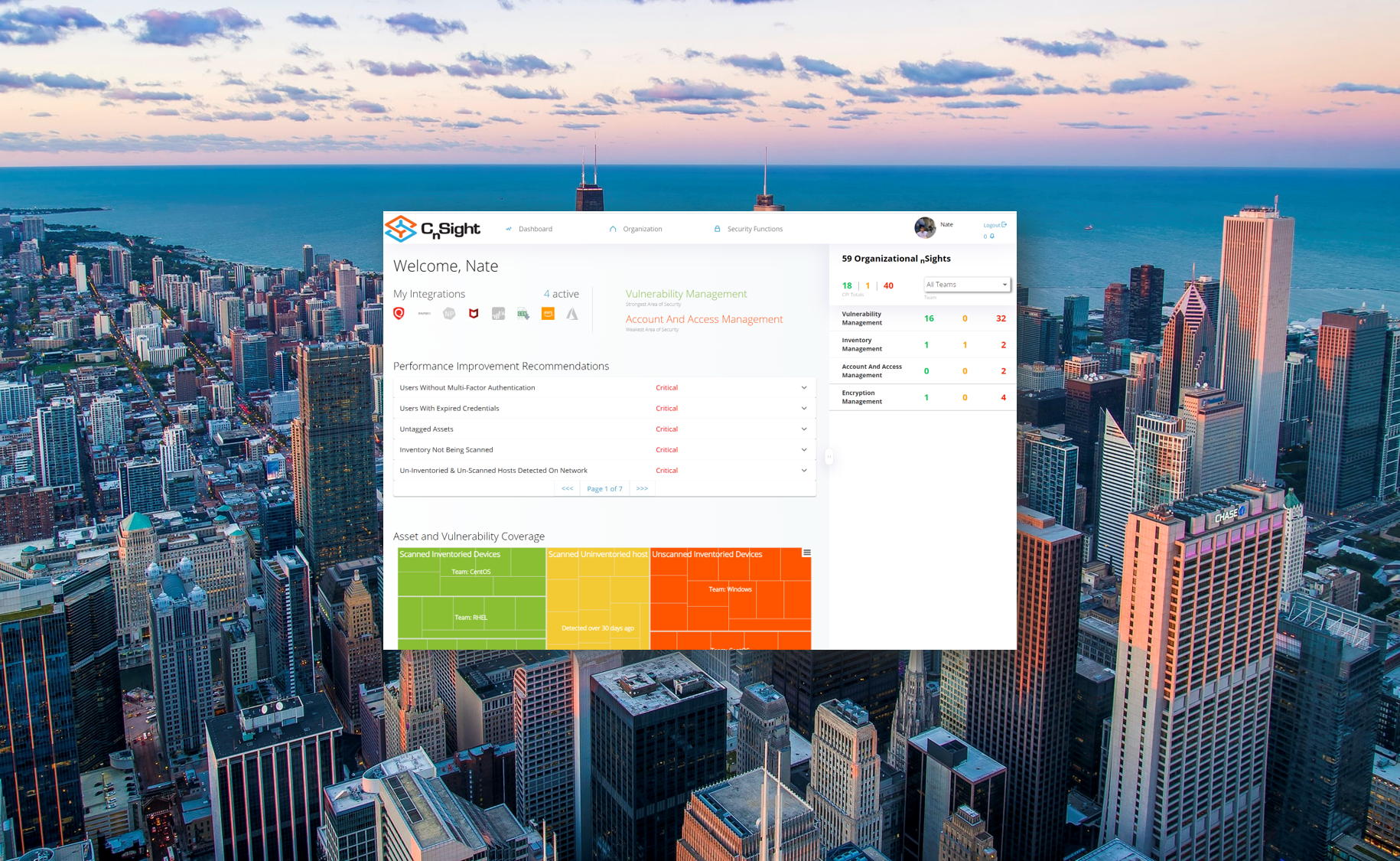
- Automate the gathering of metrics. Tracking performance without automation is exceedingly tedious and will prove to be a significant barrier to gaining visibility into cyber performance. CnSight is TDI’s answer to the growing need for visibility throughout the organization, and you can find out more here.
- Create a process for continuously reviewing and adjusting your KPIs on a regular basis. Even within a mostly static organization, external factors frequently force businesses to reevaluate what is most important to them. Review your metrics regularly to make sure that you are tracking the right things and that your teams are performing as they should.
- Have a plan for responding to data breaches. If a data breach does occur, it is important to have a plan in place for responding quickly and effectively. These plans should be tested regularly with tabletop exercises or disaster recovery simulations. In an ideal world, you should also track these metrics for increased visibility into your team’s ability to respond to security events.
Microsoft’s recent cloud data leak is a reminder that even the largest and most sophisticated technology companies are not immune to data breaches. However, by following the best practices outlined above, organizations can reduce their risk and minimize the damage if a breach does occur.