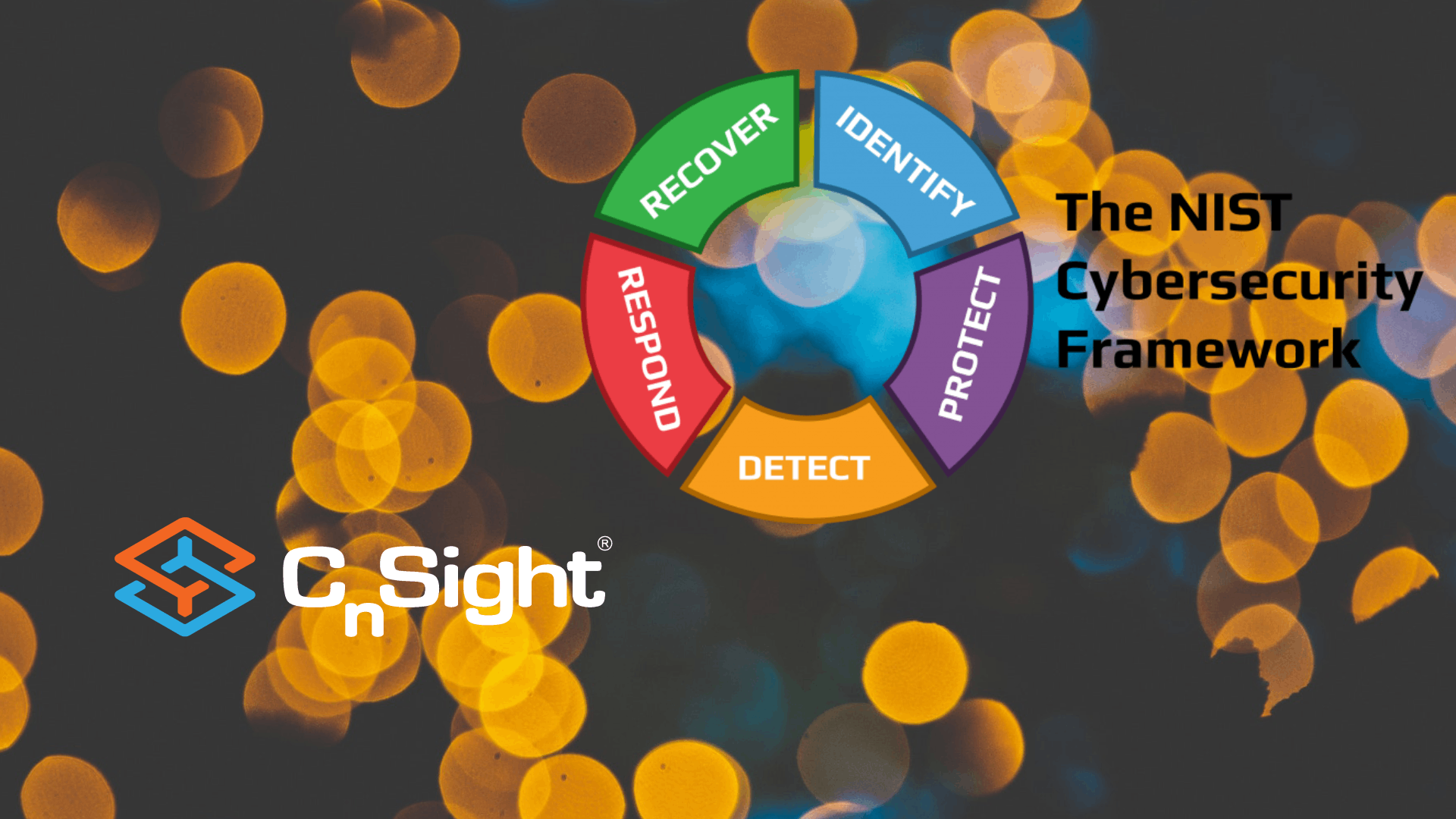
To celebrate Cyber Awareness Month, we’ve been releasing a series of posts outlining ways Cybersecurity Performance Management (CPM)TM can help you improve your cyber performance, reduce risk, and increase cyber ROI—all through the lens of the NIST Cybersecurity Framework (CSF). Last week, we talked about the “Recover” Security Function, which you can find here. Today is the last day of CPM Awareness Month, and we have one final security function to cover: Govern.
We’ve taken you from the basics of CPM through to advanced practices with a weekly series of blog posts that chronicled how CPM helps your organization align itself with each of the CSF’s Security Functions, and we hope they have helped you take actionable steps toward securing your digital future.
Cybersecurity Performance Management (CPM)
If you are new to CPM, we encourage you to check out a more in-depth blog here, where we break down what CPM is and how it fits into your organization.
But if you’re in a hurry, no problem, because we’ve got you covered. What you need to know is that CPM is the framework for effective cybersecurity and resiliency tied to your organization’s strategic cyber objectives; measuring meaningful performance metrics (defined as Cybersecurity Performance Indicators (CPIs)) – over time.
As it relates to the Framework as a whole, think of CPM as a way to supercharge how your organization aligns and benefits from implementing CSF. CPM works across functions to facilitate the visibility needed for governance and risk management. By integrating CPM practices, organizations can enhance their cybersecurity posture, align security goals with the needs of the business, and proactively protect their systems, data, and assets.
NIST CSF “Govern” Function
The final, and not yet fully released security function, is the brand new “Govern” function that is making its debut in NIST CSF 2.0. The Govern function will be what lays the groundwork for businesses to effectively regain control over the organizational aspects that are required to effectively protect yourself. The new Govern function will emphasize cybersecurity risk management governance, highlighting the critical role that cybersecurity governance plays in managing and reducing cybersecurity risk. The new function will also align cybersecurity activities with enterprise risks and legal requirements. NIST has identified these questions about cybersecurity governance and risk management as an underlying component supporting the other 5 CSF functions, necessitating a larger focus on these activities than CSF 1.1 gives credit for.
Categories that cover governance in the current version of CSF will be moved to the new Govern function. The subcategories will be expanded to create separate categories under the new function, and NIST is seeking feedback on what categories and subcategories should be incorporated into the new function. One thing that we do know is that it will inform and support the other 5 functions in the CSF, so expect these controls to be foundational to all other cybersecurity activities.
How CPM Enhances Cybersecurity Controls in the Recover Function
Cybersecurity Performance Management is a vital component in addressing cybersecurity controls within the Respond Security Function of the NIST CSF. CPM establishes clear performance metrics and cybersecurity performance indicators (CPIs) to measure the effectiveness of cybersecurity controls, which in this case helps support current and future organizational cybersecurity policy, processes, and increased visibility into business risk. These metrics provide organizations with insights into their security posture and help identify areas that require improvement. Example CPIs your organization may consider are:
- Performance metrics past due date to understand how well your team is actively reviewing cybersecurity performance metrics,
- Days since last enterprise risk assessment to better identify how consistently your organization is conducting risk assessments, and
- Organizational compliance score to measure how well you are satisfying your compliance obligations.
We have a lot of similar key metrics and dozens more in our CPM automation platform CnSight. We have found that it can be difficult, ineffective, and costly for organizations to manage cyber metrics in spreadsheets or manual workflows, so we created CnSight to help organizations get started on their CPM journey. We want to make sure that CPM is an approachable avenue to a new way of approaching and understanding cybersecurity risk, and that is a much more manageable task when you utilize automation to simplify the process.
In closing–CPM is the first big step in supercharging your NIST CSF compliance. For more reading on CPM, and to learn about how CPM intertwines with the principles of Zero Trust Architecture (ZTA), check out our recent nSight Report: Are We There Yet? From Zero, to Zero Trust. In the report, we discuss in more detail how CPM and zero trust work together to effectively implement zero trust principles in a way that doesn’t leave either the business or security teams wanting.