Risk Management is not a novel concept. In fact, my first exposure to the term was in 1996. Risk management can be applied to any number of disciplines, but the focus of this blog is cybersecurity and the linkage to business risk. While there are, and continue to be many iterations and industry monikers, at its core, the goal of risk management is to provide visibility, a shared understanding of what risks may negatively impact the business and what is being done to guard against realizing those risks.
Readers may be familiar with the many frameworks available to help organization manage risk. ISO and NIST have a series of documents, most notably in the United States, the NIST Risk Management Framework (RMF). Industry experts have also heavily shaped risk management with Gartner’s concept of Integrated Risk Management (IRM) providing for a holistic approach to risk management tying IT and cybersecurity to business objectives.
Whatever you call it and whichever framework you’re using, risk management is simple enough in theory, but depending on the nature and size of the business, organizations can find it challenging to effectively manage the risks they’ve taken the time to identify and document. That is really the key point. Anyone can identify and document a risk, but how do you ensure the underlying controls are providing an adequate level of protection at any given moment without spending an inordinate amount of time and money?
Point in time audits certainly help, as do dedicated staff assigned to the risk function. These methods don’t scale, are labor intensive, and produce results that are quick to diverge from the pace of operations, (assuming the results were even accurate to begin with). Governance Risk and Compliance (GRC) tools offered a promise to help, but turned out to be costly in customization, operation, and maintenance. For those smaller organizations, spreadsheets or home-grown databases are often used to document risks, but all need to be actively maintained and managed making these methods more of a futile documentation drill to serve an audit.
RisknSight: An Integrated & Dynamic Risk Register
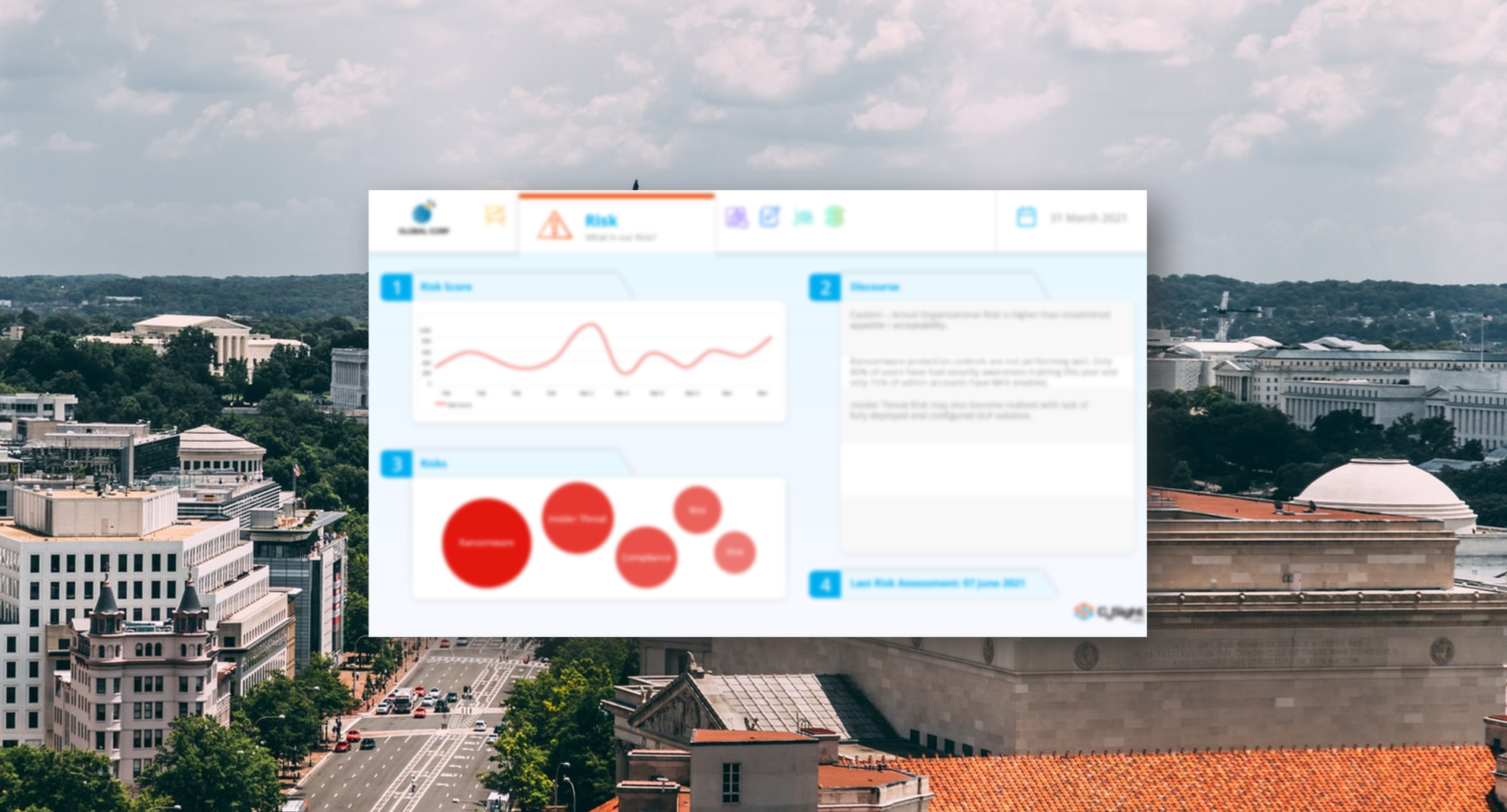
As a provider of cybersecurity expertise for the last 22 years, TDI has seen first-hand how security and risk management efforts have left many organizations in the dark, with no insight into their actual level of protection and resulting business risk. This is exactly why we developed the concept of Cybersecurity Performance Management (CPM), measured by key metrics we call Cybersecurity Performance Indicators (CPIs), all automated with our CnSight platform.
Effective in May, we’re excited to make available to our CnSight customers a new enterprise module called RisknSight which offers the ability to seamlessly create enterprise risks, assign an owner, and link threats along with our automated CPIs allowing organizations to quickly determine control performance and level of protection and impact to business risk.
Using a simple example, without CnSight and RisknSight, an organization may identify a risk of experiencing downtime to their payroll system. This risk is captured along with a corresponding threat of ransomware. As protection against this threat, the organization identified that regular vulnerability patching should be performed along with phishing training, MFA implementation, and a backup and recovery plan they can rely on when needed. With all this laid out, the team learns through interviews, policies, and past audits that the organization employs all these protections. Critical vulnerabilities are remediated every 14 days, users are trained annually, phishing exercises are performed regularly, MFA is deployed, and daily data back-ups are performed. With this understanding, the organization determines the risk of any downtime due to ransomware is low due to the number of protections in place.
This view significantly changes with CnSight and RisknSight. Having new levels of visibility, the organization can readily see the reality that critical vulnerabilities on the server haven’t been remediated in 78 days, 92% of admin users have MFA enabled, 76% of users completed annual security training, 8% of users clicked on the latest phishing exercise, and finally, there hasn’t been a successful data backup in 45 days.
This is quite a different picture indeed. Perhaps the risk of downtime due to ransomware isn’t really low at all now that we can see the reality. Business leaders can see exactly where they stand with respect to their operational cybersecurity performance and its direct impact to critical business risk.
Get more insights into the true nature of your risks from automated management. Ditch the spreadsheets and don’t overpay for more solution than you need. Streamline your approach and lower overall costs around cybersecurity and risk management with continuous monitoring from TDI and CnSight.